Mitigation of legal risks in connection with international data transfers (Schrems II)
Overview:
Why supplementary measures offered by the U.S. tools do not meet the criteria of GDPR for international transfers?
Can JENTIS provide a valid supplementary measure?
JENTIS and recommendations of data protection authorities on compliant tracking: example of CNIL proxy solution
Why do supplementary measures offered by the U.S. tools not meet the criteria of GDPR for international transfers?
Server-side services provided by U.S. companies do not ensure compliance with the GDPR, since FISA (Foreign Intelligence Surveillance Act) and the US CLOUD (Clarifying Lawful Overseas Use of Data) Act allow U.S. surveillance authorities to access data from U.S. companies, regardless of the location of the server. Therefore, if data is hosted on the server of a U.S. provider, the risk of data access by the U.S. authorities is increasingly high. In the view of the European Data Protection Authorities, the data controller (within the meaning of the GDPR) must ensure that there are supplementary measures in place that will protect personal data from re-identification or singling out.
The rulings of the data protection authorities to this effect can be found here:
Can JENTIS provide a valid supplementary measure?
Yes. When the tracking data from your website is received by the JENTIS server, you can opt for a pseudonymisation that will exclude singling-out or re-identification of the end users by the third parties. In this way, you can transfer modified data to the U.S. in line with the Schrems II requirements and convincingly exclude the risk of access by U.S. intelligence authorities as part of your Transfer Impact Assessment (TIA).
An important element of the effective supplementary measure is a proxy server based in the EU and owned by a European company. Such proxy server helps to stop direct contact between the end user device and the U.S. based third party, giving the opportunity to the website provider to modify data before it is sent to the U.S. Appropriate supplementary measures (e.g. pseudonymisation) prevent the re-identification or singling out access of U.S. intelligence services to the personal data of European users U.S. intelligence services.
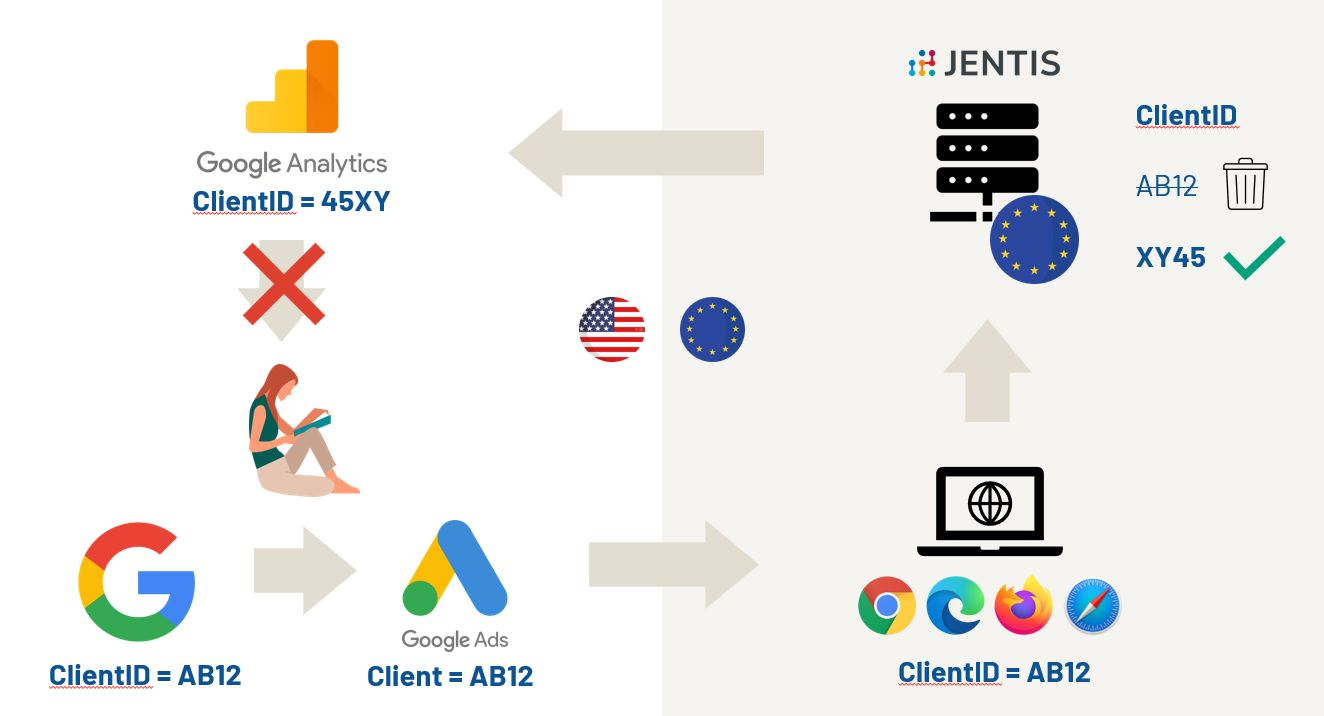
You can use JENTIS as a supplementary measure by following these steps:
First party data collected by website provider (you) is transmitted to the JENTIS Twin Server
Selected first party data points (e.g. client ID, IP address, time stamp, etc) are synthesized, pseudonymised and / or encrypted by the website provider on the JENTIS Twin Server;
The original data points are parted from the modified data points to a separate cluster on the Twin Server, the key is encrypted and kept by the website operator;
The set of modified data points (Twin Data), but not the key to original data, is forwarded by the website operator to the third party provider
JENTIS and recommendations of data protection authorities on compliant tracking: example of CNIL proxy solution
After the turmoil their Google Analytics decisions caused in the market, European data protection authorities issued recommendations for the compliant use of U.S. tools. Both the French CNIL and the Baden-Würtemberg State Commissioner recommend a proxy solution.
Specifically, CNIL lays down a set of measures that a proxy server must implement to be a valid supplementary measure for data transfers to the U.S. All the recommended measures are a configurable product feature of the JENTIS SaaS. Here is a list of the CNIL criteria compared to the technical functionality of the JENTIS SaaS.
Please mind that a final assessment whether the specific JENTIS Configuration meets the legal criteria is to be made by a professional lawyer.

JENTIS SaaS provides a flexible middleware solution for processing website data. The technical flexibility of JENTIS allows it to configure the system in line with data protection authorities' recommendations. Below you will find the list of criteria set by CNIL and the description of technical features allowing to comply with each of the criteria for proxy solution:
No transfer of the IP address to the servers of the measurement tool
JENTIS provides for a technical possibility that the IP address of the website visitor can be anonymised, pseudonymised or completely removed before being passed on to third parties. You can nonetheless attribute the country and city of the user before removing its IP address and store it in a geo-database on the web server. In this way, the original IP address of the user is never shared with the third party.

Replacement of the user ID by the proxy server
JENTIS can be configured in a way that all identifiers from Google and other third parties, such as client/user IDs, which enable a unique attribution of the user device, are not processed within the JENTIS Twin server. Instead, they will be replaced with randomly generated numbers, which are sent to the respective third party as a fictitious ID. Other data parameters enabling unique identification of users, e.g. order IDs, are also generated as a random product.
Notably, synthetic data can be used as a "supplementary measure" for data transfers outside the European Union according to the European Data Protection Supervisor (EDPS). In such a setup, the JENTIS server using its own user ID (and not the user's client) will make a request to the third party, e.g. Google, for delivery of the Analytics script.

For a technical explanation of the pseudonymization functions available in the JENTIS Tag Manager, please check our dev documentation
3)Deletion of referring website information (or referrer) external to the site
The referrer is the URL of the previous page, in the case of Google, for example, a search page, and may contain personal data. Via JENTIS, you can modify the referrers in a way that only allows conclusions to be drawn about the marketing channel, but not the user identity.
4)Deletion of any parameter contained in the URLs collected (e.g the UTMs or the URL parameters allowing the internal routing of the site)
If a user clicks on an Adwords ad, the Google ClickID (gclid) is passed to the advertising web shop in the URL as a parameter. This and similar IDs can be consistently filtered or pseudonymized via JENTIS.
5)Reprocessing of "device fingerprint" information , such as “ user-agents ”, to remove the rarest configurations that can lead to re-identification
With JENTIS you can screen out all metadata that could allow third parties to fingerprint the user device, i.e. to draw conclusions about the user. Since the timestamp could also be used for such fingerprinting, JENTIS created a new method called "Smart-Time-Framing". With JENTIS you can collect hits from a certain number of users until they are forwarded to the third party, e.g. Google, in such a timely manner so that the timestamp can no longer be used to identify the user. As a result, singling-out or re-identification of individual users is no longer possible for tracking providers in a third country.
6)No collection of identifiers between sites (cross-site) or deterministic (CRM, unique ID )
JENTIS can be configured in a way that does not collect cross-site or deterministic identifiers.
7)Deletion of any other data that may lead to re-identification
JENTIS can be configured in a way that deletes any other data parameters that may be attributed to a specific or identifiable natural person.
8)Adequate proxy hosting conditions
The JENTIS systems are hosted either on Exoscale or IONOS clouds.
Exoscale is a Swiss Company with servers in Switzerland and the EU. IONOS is a German company with servers in the EU. Both companies are ISO 27001 - certified.
Data processing outside the EU/EEA is contractually excluded between JENTIS and its cloud providers because no data transfer outside the EU/EEA is required for the provision of their service.
Our cloud providers grant us control over the location of our server instances and guarantee that any non-EU/EEA subcontractors become subprocessors only if we select server instances outside the EU/EEA.
We select exclusively EU/EEA as a processing location, thereby ensuring that only EU/EEA data centers are used for our data processing activities. Thus, in line with GDPR and the CNIL requirements, all data processing activities are performed exclusively within the EU/EEA.
In a nutshell:
JENTIS is able to provide optional configuration settings, which match the recommended proxy solution by CNIL. Pseudonymisation capability offered by JENTIS, given that the criteria set by EDPB are observed, can be used as a supplementary measure to prevent singling-out or re-identification of individual users and ensure that your tracking data can no longer be attributed to a specific or identifiable natural person without additional information.
For a detailed legal appraisal on the implementation of the requirements from the CJEU "Schrems II" ruling within the JENTIS SaaS solution, see the Schrems II Memorandum by Spirit Legal.
Please be aware that this only serves informational purposes and does not constitute legal advice.
